To enable data collection and use the alerting or the MyDataSecurity/MyDataManagement platform by your users, we invite you to fulfill the five prerequisites below.
To collect your file-share environment, IDECSI uses a LEM (Local Extractor Module) as a proxy between your local on-premises server and the SAAS monitoring platform. A local service account will allow the LEM to connect to the servers.
Creating the VM
To be fully operational for the protection of users, the LEM needs to be installed on a VM with at least the following hardware configuration:
- RAM 16 Gb
- CPU 2 core
- Disk 100 Gb
The LEM collector can run on the following operating systems:
- Windows Server 2016 Standard 64bits
- Windows Server 2019 Standard 64bits
Once the VM is created, please install Microsoft Framework .net 4.8.
Your Client Success manager will send you an email with your WorkerID and the setup.exe file to install the LEM software on the VM.
🛑 In some cases, we need to size the LEM specs according to your infrastructure, please provide us the following information about your file-shares volumetry:
- Number of files
- Total size of the file servers
- If possible the total (or average number) of accesses to the files
Opening flows
Please, verify or open the following connections:
From | To | Protocol |
I2A VM (LEM) | I2A Data Center (Internet) | TCP 443 |
I2A VM (LEM) | Server (SMB) | TCP 445 |
I2A VM (LEM) | Server (WMI) | TCP 135 |
I2A VM (LEM) | Active Directory Controller | TCP & UDP 389 |
I2A VM (LEM) | Active Directory Controller | TCP 636 |
I2A VM (LEM) | https://updates.i-2a.com/lem/wyserver.wys | TCP 443 |
NetApp (Access Policy Server) | I2A VM (LEM) | TCP 2002 |
I2A VM (LEM) | NetApp (Admin REST API) | TCP 443 |
Installing the LEM
Launch the setup.exe on the VM and proceed with the installation.
To validate the choice of the local system account versus a custom one, please read below.
Adding the proxy, 4 cases:
- No proxy: Use Local System into the LEM setup, use system default settings in the proxy configuration. Then go to Check the service account.
- Proxy but not authenticated: Use Local System into the LEM setup and use Custom Proxy settings in the proxy configuration.
Fill the URI (http://), port and set the Bypass (usually true)
Then go to Check the service account. - Proxy authenticated with the same account as the I2A service account: Use Custom User in the LEM setup and fill in the fields and use Custom Proxy settings in the proxy configuration.
Fill the URI (http://), port and set the Bypass (usually true)
Then go to Check the service account. - Proxy authenticated with another account:
- The account used for the proxy is in the same domain as the LEM: Use Custom User in the LEM setup, fill in the fields, and use Custom Proxy settings in the proxy configuration. Fill the URI and set the Bypass (usually true)
- The account used for the proxy is in a different domain than the LEM: Use the Local System and edit the settings files. Edit the proxy.config file and replace file content with:
Edit the file settings.json just after the opening bracket { and copy-paste the following (with commas):
"CustomProxy.Login": "login",
"CustomProxy.Password": "password",
"CustomProxy.ProxyAddress": "http://hostname:port",Checking the service account
At the end of the installation, you must open the MMC, stop the I2A Worker service, and set the service account login/password on it.
Then restart the I2A Worker service.
Validate the NTFS rights of the service account.
[Optional] Installing the LEM (Silent mode)
A Silent mode is available to install IDECSI LEM.
i.e.: I2AWorker 4.8.18303.0121.exe /SILENT /WorkerId=00000000-0000-0000-0000-000000000000 /IsCustomAccount=true /Username=”idecsi\svc_lem” /Password=”Password12345″
If you wish to include in a parameter a comma, vertical bar (“|”), or closing brace (“}”) inside the constant, you must escape it via “%-encoding.” Replace the character with a “%” character, followed by its two-digit hex code. A comma is “%2c”, a vertical bar is “%7c”, and a closing brace is “%7d”. If you want to include an actual “%” character, use “%25”.
Parameters
/SILENT, /VERYSILENT
Instructs Setup to be silent or very silent. When Setup is silent, the wizard and the background window are not displayed but the installation progress window is. When a setup is very silent this installation progress window is not displayed.
I2A worker parameters
/WorkerId=00000000-0000-0000-0000-000000000000
/IsCustomAccount=true|false (If necessary, Default: False)
/Username=”idecsi\svc_lem” (If IsCustomAccount = True)
/Password=”Password12345″ (If IsCustomAccount = True)
/IsCustomProxy=true|false (If necessary, Default: False)
/ProxyAddress=”http://proxy.domain.com:3128″ (If IsCustomProxy = True)
/ProxyBypassLocal=true|false (If IsCustomProxy = True)
To be operational, a service account is required. This account will allow the LEM to connect to the servers it will be in charge of.
It is therefore recommended to use a technical service account dedicated to Filer management (to prevent any risk of change in account/password).
Rights
When the LEM connects to a server to make the Discovery, the level of rights of the account used will affect the information that it will be possible to obtain.
Nevertheless, in any case, the LEM will always try to do the maximum of possible actions.
So, for example, even if the account has no rights on the server, but the settings still allow it to enter certain shares, the LEM will do it.
Discovery
The “Discovery” does not require any special rights to work.
However, if the service account has “Administrator”, “Power User”, “Print Operator”, or “Server Operator” rights, then the “LEM” will bring back more information about the configuration of the network share.
NTFS
The LEM will attempt to log in and browse through the Shares; tree browsing will be rights-based.
IDECSI cannot make a recommendation on the necessary rights, it depends very much on the company policy.
To avoid giving too many rights to the service account, some of our customers do not provide any basic rights to the account, and server by server, add NTFS rights (or position the account in the local Administrators group of the server) so that the servers can be completely collected.
Activate the Windows Server Event Logs
Access audits can be activated manually or by GPO.
This setting is accessible from your Local Security Policy application / Advanced Audit Policy Configuration / System Audit Policies – Local Group Policy Object / Object Access.

It is necessary to activate the following logs:
- Audit File Share
- Audit Detailed File Share
This setting activates the generation of events 5140, 5142, 5143, 5144, 5168, and 5145 in Event Log Security.
Please check the size of Event Log Security to keep the retention time minimal (a few hours).
This size will vary depending on server activity.
Windows Event Log Access Granting
The LEM, when ordered to do so, can remotely collect access logs generated on the server.
These logs are available in the Event Log Security.
To view them remotely, it is necessary to provide the service account with rights.
This script below makes it easier to manage the rights provided to an account on a server’s event log. You can use copy and paste it into a .ps1 file to use it.
<#
.SYNOPSIS
Grants or revokes access to an Event Log
.DESCRIPTION
Controls access to an Event Log, supporting:
Grant or revoke access
Local or domain user or group
Local or remote Event Log
Read or read/write access
Connect to remote machine as current or alternate user
Target a group of remote machines via a text file
.PARAMETER Action
The action to take (Get, Grant or Revoke)
.PARAMETER LogName
The Event Log log name (Application, Security or System)
.PARAMETER AccountName
The domain-qualified user or group name
.PARAMETER Access
The type of rights to grant (Read or ReadWrite)
.PARAMETER ComputerName
The remote computer name (optional)
.PARAMETER UserName
User name for remote computer login (optional)
.PARAMETER Password
Password for remote computer login (optional)
.PARAMETER ComputerNamesFile
Name of a text file containing computer names to affect, one name per line (optional)
.EXAMPLE
ControlEventLogPermissions.ps1 -Action 'Grant' -LogName 'Application' -AccountName 'DOMAIN\GroupName' -Access 'Read'
.EXAMPLE
ControlEventLogPermissions.ps1 -Action 'Revoke' -LogName 'System' -AccountName 'DOMAIN\GroupName' -Access 'ReadWrite' -ComputerName 'REMOTESRVR'
.EXAMPLE
ControlEventLogPermissions.ps1 -Action 'Grant' -LogName 'Security' -AccountName 'DOMAIN\GroupName' -Access 'Read' -ComputerName 'REMOTESRVR' -UserName 'DOMAIN\Admin' -Password 'SecurePwd'
.EXAMPLE
ControlEventLogPermissions.ps1 -Action 'Grant' -LogName 'Security' -AccountName 'DOMAIN\GroupName' -Access 'Read' -ComputerNamesFile 'Machines.txt' -UserName 'DOMAIN\Admin' -Password 'SecurePwd'
.NOTES
Released under The MIT License (MIT)
Copyright (c) 2015 Thomas F. Abraham (http://www.tfabraham.com)
.LINK
https://gallery.technet.microsoft.com/scriptcenter
#>
[CmdletBinding()]
Param (
[Parameter(Mandatory=$true, HelpMessage='Enter Get, Grant or Revoke')]
[ValidateSet('Get','Grant','Revoke')]
[string]$Action,
[Parameter(Mandatory=$true, HelpMessage='Enter log name')]
[string]$LogName,
[Parameter(Mandatory=$true, HelpMessage='Enter local or domain-qualified account name')]
[string]$AccountName,
[Parameter(Mandatory=$false, HelpMessage='Enter Read or ReadWrite')]
[ValidateSet('Read','ReadWrite')]
[string]$Access = 'Read',
[Parameter(Mandatory=$false, HelpMessage='Enter remote computer name')]
[string]$ComputerName,
[Parameter(Mandatory=$false, HelpMessage='Enter username for remote computer connection')]
[string]$UserName,
[Parameter(Mandatory=$false, HelpMessage='Enter password for remote computer connection')]
[string]$Password,
[Parameter(Mandatory=$false, HelpMessage='Enter name of a text file containing computer names to affect, one name per line')]
[string]$ComputerNamesFile
)
Function ConvertAccountNameToSID {
<#
.SYNOPSIS
Converts a local or domain account name to the SID
.DESCRIPTION
Converts a local or domain account name to the SID
.PARAMETER AccountName
The domain-qualified user or group name
.EXAMPLE
.NOTES
.LINK
https://gallery.technet.microsoft.com/scriptcenter
#>
[CmdletBinding()]
Param (
[Parameter(Mandatory=$true, HelpMessage='Enter local or domain-qualified account name')]
[string]$AccountName
)
[array]$accountNameParts = $null
[string]$sid = ''
[System.Security.Principal.NTAccount]$ntAcct = $null
# Split the account name to determine if it is domain-qualified
$accountNameParts = $AccountName.Split("\\")
# Attempt to convert the account name to a SID
Write-Host Translating $AccountName to SID...
if ($accountNameParts.Length -eq 1) {
$ntAcct = New-Object System.Security.Principal.NTAccount($AccountName)
}
else {
$ntAcct = New-Object System.Security.Principal.NTAccount($accountNameParts[0], $accountNameParts[1])
}
try {
$sid = $ntAcct.Translate([System.Security.Principal.SecurityIdentifier])
}
catch {
Write-Error -Message "Could not resolve account" $AccountName ". Check spelling and domain-qualify if necessary."
Return
}
Write-Host Account $AccountName has SID $sid
Write-Host
Return $sid
}
Function ControlEventLogPermissions {
<#
.SYNOPSIS
Grants or revokes access to an Event Log
.DESCRIPTION
Controls access to an Event Log
.PARAMETER Action
The action to take (Get, Grant or Revoke)
.PARAMETER LogName
The Event Log log name (Application, Security or System)
.PARAMETER AccountName
The domain-qualified user or group name
.PARAMETER Access
The type of rights to grant (Read or ReadWrite)
.PARAMETER ComputerName
The remote computer name (optional)
.PARAMETER UserName
User name for remote computer login (optional)
.PARAMETER Password
Password for remote computer login (optional)
.EXAMPLE
.NOTES
.LINK
https://gallery.technet.microsoft.com/scriptcenter
#>
[CmdletBinding()]
Param (
[Parameter(Mandatory=$true, HelpMessage='Enter Get, Grant or Revoke')]
[ValidateSet('Get','Grant','Revoke')]
[string]$Action,
[Parameter(Mandatory=$true, HelpMessage='Enter log name')]
[string]$LogName,
[Parameter(Mandatory=$true, HelpMessage='Enter local or domain-qualified account name')]
[string]$AccountName,
[Parameter(Mandatory=$false, HelpMessage='Enter Read or ReadWrite')]
[ValidateSet('Read','ReadWrite')]
[string]$Access = 'Read',
[Parameter(Mandatory=$false, HelpMessage='Enter remote computer name')]
[string]$ComputerName,
[Parameter(Mandatory=$false, HelpMessage='Enter username for remote computer connection')]
[string]$UserName,
[Parameter(Mandatory=$false, HelpMessage='Enter password for remote computer connection')]
[string]$Password,
[Parameter(Mandatory=$true, HelpMessage='Enter SID for account')]
[string]$sid
)
[array]$logConfig = ''
[array]$channelAccessArray = $null
[array]$remoteParams = $null
[array]$params = $null
[string]$channelAccess = ''
[string]$sddlRights = ''
[string]$newChannelAccess = ''
if ($Action -ieq "Grant") {
Write-Host Grant $AccountName $Access access to log $LogName on $ComputerName ...
}
elseif ($Action -ieq "Revoke") {
Write-Host Revoke $AccountName $Access access to log $LogName on $ComputerName ...
}
elseif ($Action -ieq "Get") {
Write-Host Get current access for $AccountName to log $LogName on $ComputerName ...
}
if ($ComputerName -ine '') {
$remoteParams = @("/r:""$ComputerName""")
if ($UserName -ine '') {
$remoteParams += "/u:""$UserName"""
if ($Password -ine '') {
$remoteParams += "/p:""$Password"""
}
}
}
# Get the current configuration of the desired log
Write-Host "Reading current configuration of log $LogName on $ComputerName..."
$params = @("gl", "$LogName")
$params += $remoteParams
$logConfig = & wevtutil $params
if ($LASTEXITCODE -ne 0) {
Write-Error -Message "Failed to read current configuration of log $LogName on $ComputerName"
Return
}
Write-Host "Successfully read current configuration of log $LogName on $ComputerName."
# Search for the channelAccess (permissions) configuration section
$channelAccessArray = $logConfig -like "channelAccess:*"
if ($channelAccessArray.Length -eq 0) {
Write-Error -Message "Expected to find a string starting with channelAccess. Actual: " $logConfig
Return
}
# Trim off the channelAccess label
$channelAccess = $channelAccessArray[0].Replace("channelAccess: ","")
Write-Debug -Message "Current channelAccess for $LogName on $ComputerName is $channelAccess"
if ($Action -ieq "Grant") {
# Search for an existing SDDL token using the target SID
if ($channelAccess -match "(\(\w*\;\w*\;\w*\;\w*\;\w*\;$sid\))") {
# Remove the existing SDDL token
$channelAccess = $channelAccess.Replace($matches[0], "")
}
# Convert the permissions string to SDDL
if ($Access -ieq "ReadWrite") {
$sddlRights = "0x3"
}
else {
$sddlRights = "0x1"
}
# Build and append a new SDDL onto the existing SDDL
$newChannelAccess = $channelAccess + "(A;;" + $sddlRights + ";;;" + $sid + ")"
}
elseif ($Action -ieq "Revoke") {
# Search for an existing SDDL token using the target SID
if ($channelAccess -match "(\(\w*\;\w*\;\w*\;\w*\;\w*\;$sid\))") {
# Remove the existing SDDL token
$newChannelAccess = $channelAccess.Replace($matches[0], "")
}
else {
Write-Host "SID does not exist in channel access string on $ComputerName. Nothing to revoke." -ForegroundColor Yellow
Return
}
}
elseif ($Action -ieq "Get") {
# Search for an existing SDDL token using the target SID
if ($channelAccess -match "(\(\w*\;\w*\;\w*\;\w*\;\w*\;$sid\))") {
if ($matches[0].Contains("0x3")) {
Write-Host "$AccountName currently has READ/WRITE access to $LogName on $ComputerName." -ForegroundColor Green
}
elseif ($matches[0].Contains("0x1")) {
Write-Host "$AccountName currently has READ access to log $LogName on $ComputerName." -ForegroundColor Green
}
else {
Write-Host "$AccountName currently has an UNKNOWN access right to log $LogName on $ComputerName." -ForegroundColor Green
}
}
else {
Write-Host "$AccountName currently has NO access rights to log $LogName on $ComputerName." -ForegroundColor Green
Return
}
Return
}
Write-Debug -Message "New channel access string is $newChannelAccess"
# Write the updated configuration
Write-Host "Writing new channel access string to log $LogName configuration on $ComputerName ..."
$params = @("sl", "$LogName", "/ca:$newChannelAccess")
$params += $remoteParams
& wevtutil $params
if ($LASTEXITCODE -ne 0) {
Write-Error -Message "Failed to write new configuration of log $LogName on $ComputerName"
Return
}
Write-Host "Done writing new configuration of $LogName on $ComputerName." -ForegroundColor Green
}
[hashtable]$scriptParameters = $PSBoundParameters
[array]$computerNamesFileContent
[string]$listComputerName
[string]$sid
$Error.Clear()
Try {
$sid = ConvertAccountNameToSid -AccountName "$AccountName"
$scriptParameters['sid'] = $sid
$scriptParameters.Remove('ComputerNamesFile')
if ($ComputerNamesFile -ieq '') {
if ($scriptParameters.ContainsKey("ComputerName") -eq $false) {
$scriptParameters["ComputerName"] = $env:COMPUTERNAME
}
ControlEventLogPermissions @scriptParameters
}
else {
$computerNamesFileContent = Get-Content $ComputerNamesFile
foreach ($listComputerName in $computerNamesFileContent) {
$scriptParameters["ComputerName"] = $listComputerName
ControlEventLogPermissions @scriptParameters
}
}
}
Catch {
Write-Error -Message $Error[0].Exception.Message
}Activate NetApp Event log
FPOLICY commands to register a LEM
Legend:
- VSERVER_ADMIN (Cluster Level)
- VSERVER_NODE (Cluster’s node)
- VSERVER_DATA (File server)
- value: Proposal of name, can be changed
- [value]: Insert appropriated value
Global commands
Logging
fpolicy policy event create -vserver [VSERVER_ADMIN] -event-name fp_event_idecsi_cifs -file-operations create,create_dir,open,delete,delete_dir,read,write,rename,rename_dir,setattr -protocol cifs -filters first-read,first-write,open-with-delete-intent
fpolicy policy external-engine create -vserver [VSERVER_ADMIN] -engine-name fp_ex_eng -primary-servers [LEM_IP] -port 2002 -extern-engine-type asynchronous -ssl-option no-auth Allow the LEM to self-reconnect
security login rest-role create -vserver [VSERVER_ADMIN] -role rest_role_idecsi -api "/api/protocols/fpolicy" -access all
security login create -user-or-group-name svc_rest_idecsi -application http -authmethod password -role rest_role_idecsi -vserver [VSERVER_ADMIN] Commands per server to be collected
fpolicy policy create -vserver [VSERVER_DATA] -policy-name IDECSI -events fp_event_idecsi_cifs -engine fp_ex_eng -is-mandatory false
fpolicy policy scope create -vserver [VSERVER_DATA] -policy-name IDECSI -volumes-to-include "*" -export-policies-to-include "*"
fpolicy enable -vserver [VSERVER_DATA] -policy-name IDECSI -sequence-number 5 Debug Commands to ensure status, or restart events publication
vserver fpolicy policy event show fp_event_idecsi_cifs -instance
fpolicy policy external-engine show
fpolicy show-engine
vserver fpolicy show
vserver fpolicy show -vserver [VSERVER_DATA]
fpolicy policy scope show -vserver [VSERVER_VM] - policy-name [IDECSI]
fpolicy engine-connect -node [NODE] -vserver [VSERVER_VM] -policy-name [IDECSI] -server [LEM_IP]
network ping -lif [LIF_NAME] -destination [LEM_IP] -show-detail[Optionnal] Encrypted NetApp Service Account settings
To insert in the encrypted file
|---------------------------|------------------------------|
| Key | Value |
|---------------------------|------------------------------|
| NetAppRestApiBaseUri | http://servername |
| NetAppRestApiLogin | username |
| NetAppRestApiPwd | password |
|---------------------------|------------------------------|To enable users to connect to their MyDataSecurity or MyDataManagement, we can integrate your identity federation. Below is the procedure with Azure AD. For other solutions, please consult the knowledge base.
| 1. Go to your administrator Dashboard in Azure Active Directory | |
| and click on Active Directory > Enterprise Applications |  |
| 2. Click + Create your own application |  |
| Type a relevant name in Input Name (ie I2A Platform), select the “Integrate any other application you don’t find in the gallery (non-gallery)” option, and click Create. |  |
| 3. After this, you’re redirected to the newly created application Overview, go to Assign users and groups from the tile or the side menu. |  |
| 4. If you want to restrain the usage, you can add users and/or groups you want to access the I2A platform. We recommend adding a group with all your tenant users, I2A will recognize the users with an account. |  |
| 5. Go to Single sign-on from the side menu and select SAML as the single sign-on method. |  |
| 6. Click on Upload metadata file and select the XML file provided by your Client Success Manager. | 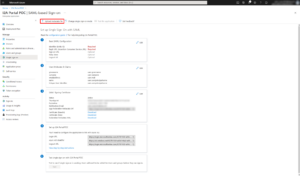 |
| 7. After the import, you’ll have: | 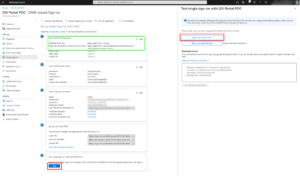 |
In the Basic SAML configuration block: Identifier (Entity ID): https://dcxx-auth.i-2a.com You can now test your authentication using the Test button. | |
| 8. Please send us the Federation metadata XML file to clientsuccess@idecsi.com | 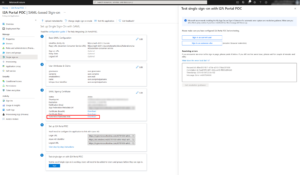 |
Your Client Success Manager will inform you after your metadata has been integrated.
To encourage users to adopt the solution, we propose the use of an application that will enable our platform to send e-mails from your Microsoft tenant. If not, IDECSI will use Graph API to send emails from a generic address (alerts@idecsi.com).
If you want to use a particular email address of your domain, we can use the Microsoft Graph API to send IDECSI emails through an application granted on your tenant.
IDECSI proposes to use the generic application “I2A Mail Sender” to send notifications.
The application used to send notifications cannot be the same as the one used for the remediation, as the permission “Mail.Send” must be scoped on the account.
Step 1: Grant permission to this application
The following step is to grant the application with Global Administrator rights. Here is the link to grant the generic IDECSI managed app :
https://login.microsoftonline.com/common/adminConsent?client_id=ba28a8f5-601a-4523-a7e9-570dc40d49d7
The only permission to be granted is:
| Permission | Display String | Description | Admin Consent required |
| Mail.Send | Send mail as a user | Allows the app to send mail as users in the organization | Yes |
More information on the permission: Microsoft Graph permissions reference – Microsoft Graph | Microsoft Docs
Step 2: Enforce a restriction policy to limit the scope of the permission
To guarantee the best possible security, and to limit the permissions of the application granted in step 2, it is necessary to limit the right to send mail to a single service account used for this purpose.
For this, it is necessary to create an ApplicationAccessPolicy.
#0. Select the application you want to configure:
$myAppId = {my app id}
#1. Connect to Exchange Online with the ExchangeOnlineManagement PowerShell module
Connect-ExchangeOnline
#2. Create a mail-enabled security group that contains all the accounts you want to send mails from
$myRestrictedGroup = New-DistributionGroup -Name "Mail service accounts" -Type "Security" -Members @("senderemail@mydomain.com")
#3. Optionally hide the group from the address list
Set-DistributionGroup -Identity $myRestrictedGroup.Identity -HiddenFromAddressListsEnabled $true
#4. Create the application access policy to only allow sending the app mails for the specified distribution group
$params = @{
AccessRight = "RestrictAccess"
AppId = $myAppId
PolicyScopeGroupId = $myRestrictedGroup .PrimarySmtpAddress
Description = "Restrict I2A Sender Mail app permissions to only allow access to service account"
}
New-ApplicationAccessPolicy @paramsFrom this point, the application “I2A Mail Sender” will be authorized only for the sender e-mail address wanted “senderemail@mydomain.com”
More information:
- Limiting application permissions to specific Exchange Online mailboxes – Microsoft Graph | Microsoft Docs
- Securely sending emails from PowerShell scripts with modern authentication enforced – nicolonsky tech
- New-ApplicationAccessPolicy (ExchangePowerShell) | Microsoft Docs
Step 3: Communicate to your Client Success Manager the email address authorized.
Your Client Success Manager will then configure the email address as the account used to send notifications to end-users and security teams.
- The email address that will be used to send emails (and the aliases)
- Application ID
- App Secret