As part of the Detox offer, IDECSI provides you with an example of a communication campaign and sample e-mails to send.
The emails sent by the platform will be campaign emails and reminders to users who have not consulted their security profile. Other e-mails should be sent using your usual tools. |
Click here to view the communication campaign kit and the sample emails that can be downloaded:
To enable data collection and the use of the MyDataSecurity/MyDataManagement platform by your users, we invite you to fulfill the seven prerequisites below.
💡 There are some differences between the requirements for MyDataSecurity and MyDataManagement. Please read carrefully the tabs below to get the right information.
💡 This tab is relevant for both MyDataSecurity and MyDataManagement configurations.
The solution uses Microsoft APIs to collect permissions and access to Exchange, OneDrive, SharePoint, and Teams.
Remediation is also carried out via the APIs.
Granting the permissions to the IDECSI-Platform app
Please send us your TenantID, your Primary Domain, your SharePoint root site URL ([yourdomain].sharepoint.com) and let us know when you have granted the app IDECSI – Platform below by clicking the following links and logging in as administrator of the tenant:
https://login.microsoftonline.com/common/adminconsent?client_id=52e3a6c9-b6cc-4854-92db-06afc774da14
Application permissions details for the granted app
| API | Permission | IDECSI Usage | More? |
| Office 365 Management API | ActivityFeed.Read | Collect audit logs to display access events in MyDataSecurity. Detect changes in rights and permissions to be able to recollect the resources, and also alert if needed. | Office 365 Management Activity API reference | Microsoft Learn |
| Graph API | AuditLog.Read.All | Collect unified audit logs and Entra audit logs to enrich all Idecsi’ Resource’s information. | |
| Graph API | ChannelSettings.Read.All | Map Teams channels (private and shared) to be displayed in MyDataSecurity. | List channels – Microsoft Graph v1.0 | Microsoft Learn |
| Graph API | Channel.Delete.All | Perform remediation on a private or shared Teams channel from MyDataSecurity. | Get conversationMember – Microsoft Graph v1.0 | Microsoft Learn Remove member from channel – Microsoft Graph v1.0 | Microsoft Learn |
| Graph API | ChannelMember.ReadWrite.All | Identify channel members and remediate a member directly from MyDataSecurity. | Delete channel – Microsoft Graph v1.0 | Microsoft Learn |
| Graph API | DelegatedPermissionGrant.ReadWrite.All | Identify and remediate delegated permissions through the Application tab in MyDataSecurity. | Delete oAuth2PermissionGrant (a delegated permission grant) – Microsoft Graph v1.0 | Microsoft Learn |
| Graph API | Directory.Read.All | Identify users, groups, and applications to display this information in MyDataSecurity. | Required for AD information (users, groups, licenses, applications, administrators) |
| Graph API | User.Read | Authenticate users for MyDataSecurity (SSO). | Delegated Permission for SSO |
| Graph API | Users.Read.All | Associate the user’s profile picture with their IDECSI interfaces. | Required to get the user’s profile picture |
| Graph API | Files.ReadWrite.All | Perform version and file remediations through MyDataManagement and remediate sharing permissions in MyDataSecurity. | Remove access to an item – Microsoft Graph v1.0 | Microsoft Learn Delete permission – Microsoft Graph v1.0 | Microsoft Learn |
| Graph API | Group.ReadWrite.All | Remediate groups (owners, members, guests), modify privacy settings (public/private), or delete them. | Remove member – Microsoft Graph v1.0 | Microsoft Learn Remove group owner – Microsoft Graph v1.0 | Microsoft Learn Add owners – Microsoft Graph v1.0 | Microsoft Learn Update group – Microsoft Graph v1.0 | Microsoft Learn Delete group – Microsoft Graph API – Microsoft Graph v1.0 | Microsoft Learn |
| Graph API | InformationProtectionPolicy.Read.All | Retrieve sensitivity label configurations (Purview). | List sensitivityLabels – Microsoft Graph beta | Microsoft Learn |
| Graph API | MailboxSettings.Read | Adapt language and settings for the IDECSI interface and identify the mailbox associated with a user. | Get user mailbox settings – Microsoft Graph v1.0 | Microsoft Learn |
| Graph API | Policy.Read.All | Read tenant configurations and alert in case of changes. | Required to read configurations |
| Graph API | Reports.Read.All | Collect various reports to enrich information in MyDataSecurity and MyDataManagement. | reportRoot: getOneDriveUsageStorage – Microsoft Graph v1.0 | Microsoft Learn reportRoot: getOneDriveUsageFileCounts – Microsoft Graph v1.0 | Microsoft Learn reportRoot: getSharePointSiteUsageStorage – Microsoft Graph v1.0 | Microsoft Learn reportRoot: getSharePointSiteUsageFileCounts – Microsoft Graph v1.0 | Microsoft Learn |
| SharePoint | Sites.FullControl.All | Collect (classic site administrators) and correct permissions (Everyone site admin, EEEU site admin, Everyone, EEEU) on SharePoint sites, and retrieve the sharing link creator and creation date. | SharePoint admin APIs authentication and authorization | Microsoft Learn |
| Graph API | Sites.Read.All | Map sites, libraries, permissions, and metadata used to populate user profiles in MDS/MDM. | List sites – Microsoft Graph v1.0 | Microsoft Learn |
| Graph API | TeamSettings.Read.All | Map Teams teams and their settings to populate user profiles in MDS. | Get team – Microsoft Graph v1.0 | Microsoft Learn |
| Office 365 Exchange Online API | Exchange.ManageAsApp | Permission that grants no rights to the application itself. The associated service principal will receive collection and remediation rights (via PowerShell) depending on the assignment. | Authenticate an EWS application by using OAuth Application Access Policy Support Added to Exchange Web Services in Exchange Online Role-Based Access Control for Applications in Exchange Online |
You can find details here on Why do we need the permissions Sites.ReadWrite.All & Sites.FullControl (CSOM/REST) – IDECSI Help Center (you need to create an account)
More information on permissions: Overview of Microsoft Graph permissions – Microsoft Graph | Microsoft Learn
Providing rights on Exchange
The “Manage Exchange as Application” right allows connecting as an application but does not grant any specific permissions. That is why we need to add a “Service Principal” that will enable its use. To limit rights, we will create an I2A Role Group, where we will place the “Service Principal”.
⚠️ Please note:
- Install or update PowerShell to version 7 (
winget install --id Microsoft.Powershell --source winget) - Launch PowerShell 7 as the local administrator of the machine (or with an account that has the required rights)
- Install the Microsoft.Graph module (
Install-Module Microsoft.Graph) - Install the ExchangeOnlineManagement module version 3.6 (
Install-Module -Name ExchangeOnlineManagement -RequiredVersion 3.6.0).
# Import ExchangeOnline module and Graph module
Import-Module ExchangeOnlineManagement;Get-Module ExchangeOnlineManagement
Import-Module Microsoft.Graph;Get-Module Microsoft.Graph
# Load and connect to Microsoft Graph with administrator rights.
Connect-MgGraph -Scopes AppRoleAssignment.ReadWrite.All,Application.Read.All
# Retrieve the Service Principal corresponding to the "IDECSI - Platform" application.
$AzureADApp = Get-MgServicePrincipal -Filter "DisplayName eq 'IDECSI - Platform'"
# Exchange Online Connexion
# This prompts for user credentials. Please use an Exchange Admin account to connect.
Connect-ExchangeOnline
# Create an Exchange Service Principal linked to the Azure AD App
New-ServicePrincipal -AppId $AzureADApp.AppId -ObjectId $AzureADApp.Id -DisplayName "SP for Azure AD App IDECSI - Platform"
# Retrieve the new Service Principal object
$SP = Get-ServicePrincipal -Identity "SP for Azure AD App IDECSI - Platform"
Write-Host ($SP | Format-Table | Out-String)
# Define variables
# These variables store:
# * The name of the role group
$roleGroupName = "I2A"
# * The names of custom management roles to be created.
$roleName = "Mail Recipients - ViewOnly - I2A"
$roleName1 = "Remediation - I2A"
$roleName2 = "Remediation 2 - I2A"
# Create Role: "Mail Recipients - ViewOnly - I2A"
# Creates a new management role based on the "Mail Recipients" parent role.
New-ManagementRole $roleName -Parent "Mail Recipients"
Get-ManagementRoleEntry ($roleName + "\*")
$data2 = Get-ManagementRoleEntry ($roleName + "\*")
# This loop removes all cmdlets except those starting with "Get", effectively making the role read-only.
foreach($data in $data2)
{
$name = ""
$name = $data.Name
if($name -NotLike "Get*")
{
Remove-ManagementRoleEntry $roleName\$name -confirm:$false
Write-Host ("Done for $name")
}
}
# Create Role: "Remediation - I2A"
# Creates another role based on "Mail Recipients".
New-ManagementRole $roleName1 -Parent "Mail Recipients"
Get-ManagementRoleEntry ($roleName1 + "\*")
$entries = Get-ManagementRoleEntry ($roleName1 + "\*")
# This time, it keeps only specific "Remove" cmdlets (like Remove-MailboxPermission, etc.), making the role strictly focused on remediation tasks, like removing permissions or inbox rules.
foreach($entry in $entries)
{
$name = ""
$name = $entry.Name
if ($name -NotLike "Remove-MailboxPermission" -And $name -NotLike "Remove-InboxRule" -And $name -NotLike "Remove-MailboxFolderPermission" -And $name -NotLike "Remove-RecipientPermission" -And $name -NotLike "Remove-ADPermission")
{
Remove-ManagementRoleEntry $roleName1\$name -Confirm:$false
Write-Host ("Done for $name")
}
}
# Create Role: "Remediation 2 - I2A"
# Creates a third custom role based on "Mail Recipient Creation".
New-ManagementRole $roleName2 -Parent "Mail Recipient Creation"
Get-ManagementRoleEntry ($roleName2 + "\*")
$entries = Get-ManagementRoleEntry ($roleName2 + "\*")
# This removes all cmdlets except Set-MailboxFolderPermission, allowing the role to only modify folder permissions, again focusing on a specific remediation use case.
foreach($entry in $entries)
{
$name = ""
$name = $entry.Name
if ($name -NotLike "Set-MailboxFolderPermission")
{
Remove-ManagementRoleEntry $roleName2\$name -Confirm:$false
Write-Host ("Done for $name")
}
}
Get-ManagementRoleEntry ($roleName + "\*")
Get-ManagementRoleEntry ($roleName1 + "\*")
Get-ManagementRoleEntry ($roleName2 + "\*")
# Assign Roles to Role Group and Add Service Principal
# Creates a new role group named "I2A", includes:
# * Standard built-in roles (like audit and read-only)
# * The 3 custom roles we created
# * Assigns everything to the Service Principal
New-RoleGroup -Name $roleGroupName -Roles "Audit Logs","View-Only Configuration","View-Only Recipients",$roleName,$roleName1,$roleName2 -Members $SP.Identity
# Disconnect
# Ends the Exchange Online and Graph session properly.
Disconnect-ExchangeOnline
Disconnect-GraphOnce the application is granted and the script ran successfully, please let your Customer Success Manager know it.
💡 This tab is relevant for both MyDataSecurity and MyDataManagement configuration.
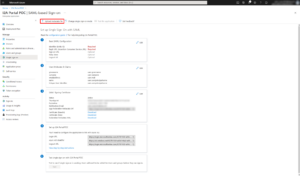
To enable users to connect to their MyDataSecurity or MyDataManagement, we can integrate your identity federation. Below is the procedure with Azure AD. For other solutions, please consult the knowledge base.
Your Client Success Manager will inform you after your metadata has been integrated.
💡 This tab is relevant for both MyDataSecurity and MyDataManagement configurations.
To collect your users’ information and attach their resources, we have to set up a request based on your Azure Directory content. This request allows us to automatically import the necessary data.
The request can be based on two types of information to filter the appropriate scope of users:
- AD Attributes configured for each user. The most common attributes used for the request are the Microsoft License Plans’ SkuIDs.
- One or more AD Groups containing the users
To proceed with the request setup, please provide your Client Success Manager with the relevant type of information (attribute or group). If needed, your Client Success Manager will be happy to assist you with this process.
Anonymous reporting
Microsoft reports shows anonymous user names instead of actual user names. Those reports are required for MyDataManagement collects, but the user identity is required in order to show him information about his data on his MyDataManagement profile.
This setting is also required to display Microsoft 365 Groups data in the MyDataSecurity BI dashboard.
Therefore, it is mandatory to deactivate the anonymous reporting on your tenant.
To do so, please follow the tutorial here.
💡 This tab is relevant for both MyDataSecurity and MyDataManagement configurations.
To encourage users to adopt the solution, we propose using an application that will enable our platform to send emails from your Microsoft tenant. If not, IDECSI will use Graph API to send emails from a generic address ().
If you want to use a specific email address of your domain, we can use the Microsoft Graph API to send IDECSI emails through an application granted on your tenant. You need to use an account from your tenant with at least a licence including Microsoft Exchange Online P1 or P2.
⚠ Mailing lists are not supported.
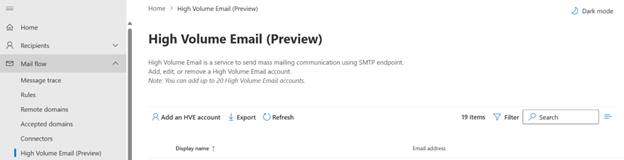
Depending on the number of recipients you plan to target through your campaigns, you will need to use Microsoft’s High volume email (HVE) service.
HVE: For 5 000 to more than 150 000 recipients
What is HVE (High Volume Email)?
Step 1: Create your HVE account
Navigate to https://admin.exchange.microsoft.com/.
- Under the Mail flow menu, select High Volume Email(Preview).
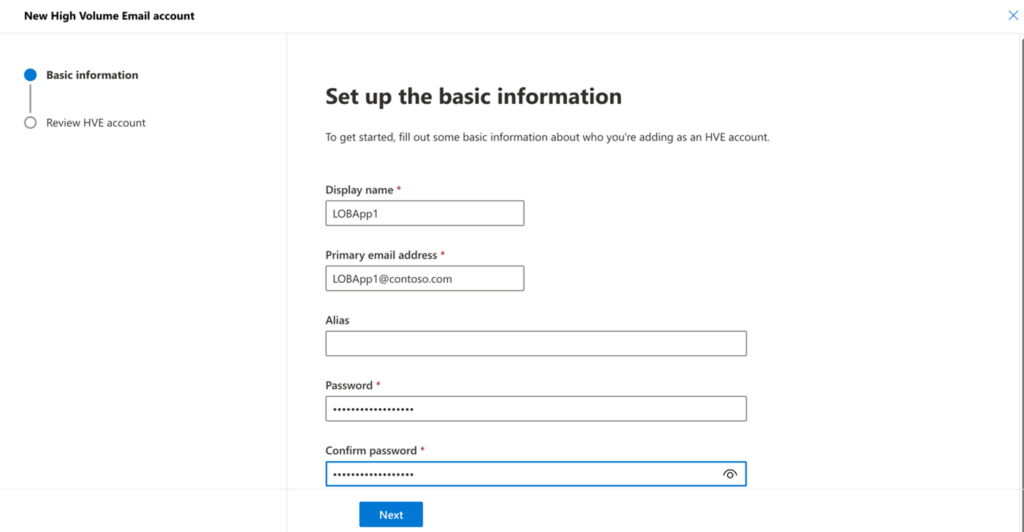
Provide a valid display name. Primary address should be in the following format: , where contoso.com should be within a list of accepted domains, alias (optional), and password.
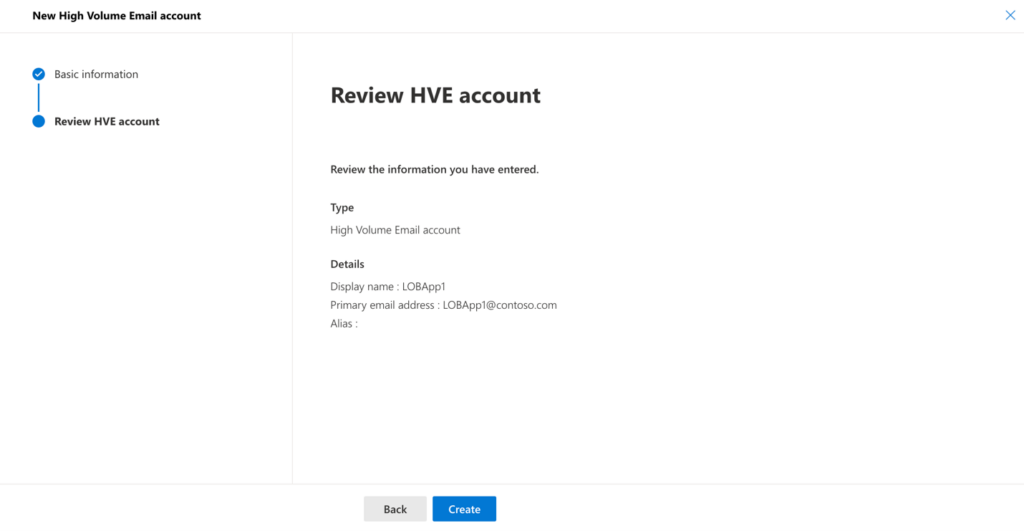
Validate provided information.
Select Create.
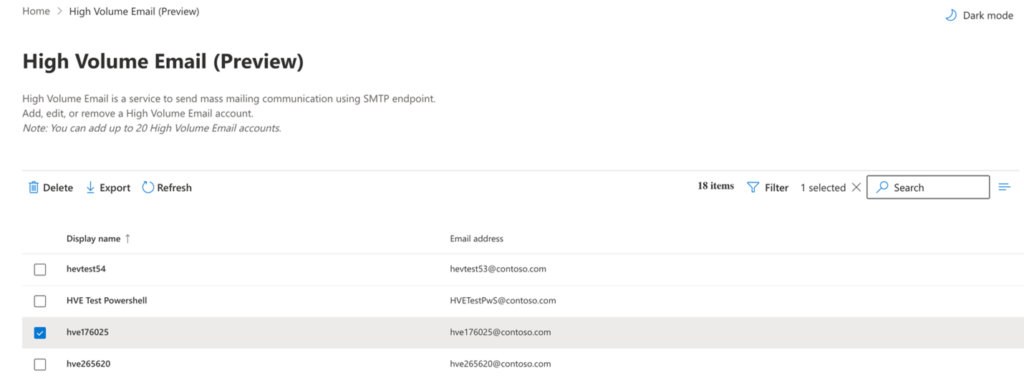
The new HVE account is listed in the HVE accounts list.
Step 2: Grant Consent
- Please, open a private navigator page
- Go to: IDECSI Platform HVE
- Sign in with your HVE account
- You will see a consent request screen for the application
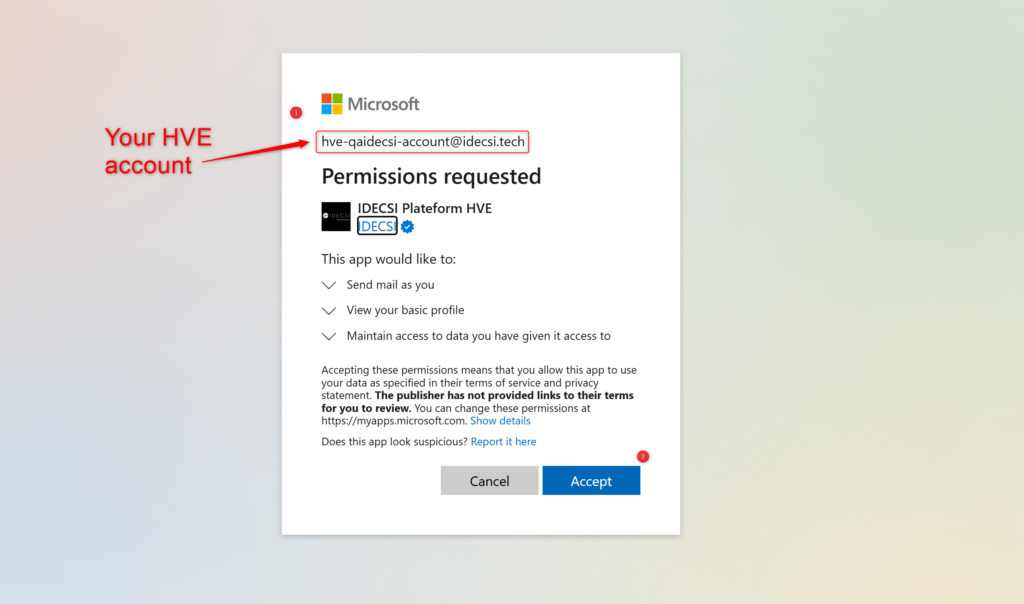
- Click “Accept” to approve
- Once completed, please share the account’s email address and password with your IDECSI Customer Success Manager contact.
Step 3: App Integration in “Identities” (handled by IDECSI)
Step 4. Sending Test
Classic: For 1 to 4 999 recipients
IDECSI proposes to use the generic application “I2A Mail Sender” to send notifications.
The application used to send notifications cannot be the same as the one used for the remediation, as the permission “Mail.Send” must be scoped on the account.
Step 1: Grant permission to this application
The following step is to grant the application Global Administrator rights. Here is the link to grant the generic IDECSI-managed app
https://login.microsoftonline.com/common/adminConsent?client_id=ba28a8f5-601a-4523-a7e9-570dc40d49d7
The only permission to be granted is:
| Permission | Display String | Description | Admin Consent required |
| Mail.Send | Send mail as a user | Allows the app to send mail as users in the organization | Yes |
More information on the permission: Microsoft Graph permissions reference – Microsoft Graph | Microsoft Docs
Step 2: Enforce a restriction policy to limit the scope of the permission
To guarantee the best possible security, and to limit the permissions of the application granted in step 2, it is necessary to limit the right to send mail to a single service account used for this purpose.
For this, it is necessary to create an ApplicationAccessPolicy.
#0. Select the application you want to configure:
$myAppId = {my app id}
#1. Connect to Exchange Online with the ExchangeOnlineManagement PowerShell module
Connect-ExchangeOnline
#2. Create a mail-enabled security group that contains all the accounts you want to send mails from
$myRestrictedGroup = New-DistributionGroup -Name "Mail service accounts" -Type "Security" -Members @("CHOSEN EMAIL ADDRESS")
#3. Optionally hide the group from the address list
Set-DistributionGroup -Identity $myRestrictedGroup.Identity -HiddenFromAddressListsEnabled $true
#4. Create the application access policy to only allow sending the app mails for the specified distribution group
$params = @{
AccessRight = "RestrictAccess"
AppId = $myAppId
PolicyScopeGroupId = $myRestrictedGroup.PrimarySmtpAddress
Description = "Restrict I2A Sender Mail app permissions to only allow access to service account"
}
New-ApplicationAccessPolicy @paramsFrom this point, the application “I2A Mail Sender” will be authorized only for the sender e-mail address wanted, “”
More information:
- Limiting application permissions to specific Exchange Online mailboxes – Microsoft Graph | Microsoft Docs
- Securely sending emails from PowerShell scripts with modern authentication enforced – nicolonsky tech
- New-ApplicationAccessPolicy (ExchangePowerShell) | Microsoft Docs
Step 3: Communicate to your Client Success Manager the email address authorized.
Your Client Success Manager will then configure the email address as the account used to send notifications to end-users and security teams.
- The email address that will be used to send emails (and the aliases)
💡 This tab is relevant for both MyDataSecurity and MyDataManagement configuration.
To encourage user adoption, we propose using a personalized URL to access our platform. Without customization, the URL will look like this: https://dc01.i-2a.com/app/my-data-security/tenants/xxxxxxxxxx/dashboard
How to customize the URL?
- Choose the desired URL and create the corresponding entry on your DNS
- Provide us with the chosen domain name
- Provide us with the corresponding SSL certificate and the private key with its password (.pem format if possible)
We will let you know when the redirection to your URL is done, and give you the CNAME or A information for the DNS entry.
💡 This tab is relevant for both MyDataSecurity and MyDataManagement configuration.
To encourage users to adopt the solution, we offer to customize the Emails, Interfaces, intended for them.
Here are the elements that can be customized on the email templates:
| 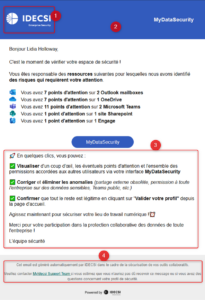 |
Loading Screen
Here are the elements that can be customized on the loading screen of MyDataSecurity:
| 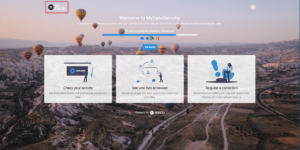 |
On the Home Page
Here are the elements that can be customized on the main interface of MyDataSecurity: