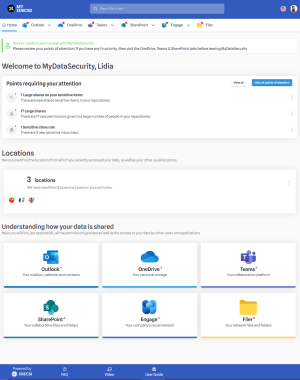
Homepage
Your profile homepage : the dashboard
This home page contains your MyDataSecurity Dashboard, where you’ll find the following items:
☑ Navigation tools for easy access to the security elements of your Microsoft 365 environment
☑ A summary of identified points of attention that need to be reviewed
☑ Your synchronized devices
☑ Your usual countries of connection
☑ Additional corporate resources to help you master your MyDataSecurity profile.
Top, menu and banner
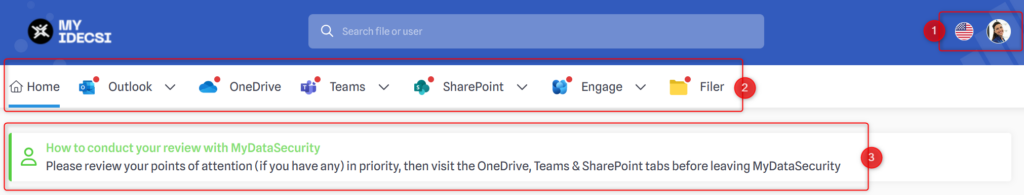
You can choose the language among 15 possibilities if you click on the country logo. If you click on your profile picture, you can access information about your profile, such as the operations history, or your account information (name, phone number, etc.)
Access tabs to your protected Microsoft 365 applications. The presence of a red dot indicates the presence of important points of attention;
- Optional company information banner.
Points of attention (POAs) highlight the most significant security threats in your profile, for example:
☑ Sharing of sensitive files based on the labels provided by your classification system (AIP/MIP)
☑ External, anonymous, extended file sharing
☑ External e-mail transfers
☑ Etc.
when you open your profile, you might see a blue rectangle with information about your POAs. If you don’t see this menu, please go directly to the next tab “Points of Attention (POAs)”
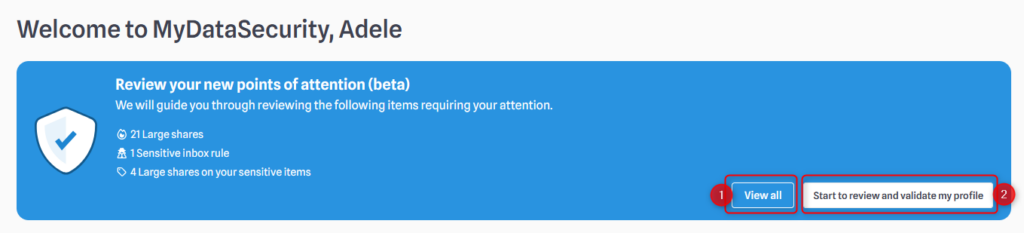
- If you click on “View All,” you will see the list of all your POAs. By clicking on a specific POA, you will be redirected to the corresponding tab, whether it is an Exchange, OneDrive, Teams, or SharePoint POA. You will find more detailed information about managing your data on the pages related to the corresponding resource.
- This button launches the Security Checkup process: you will be able to manage all your POAs at once through a clear and guided interface.
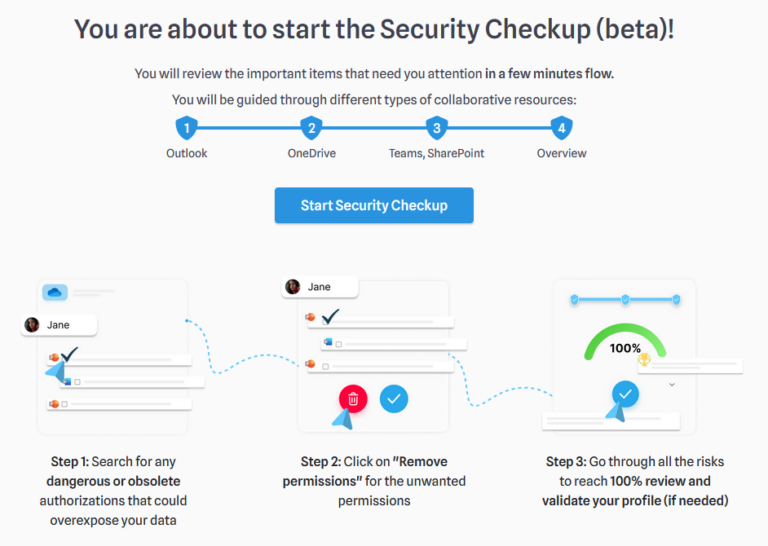
Click on “Start Security Checkup” to begin the process :
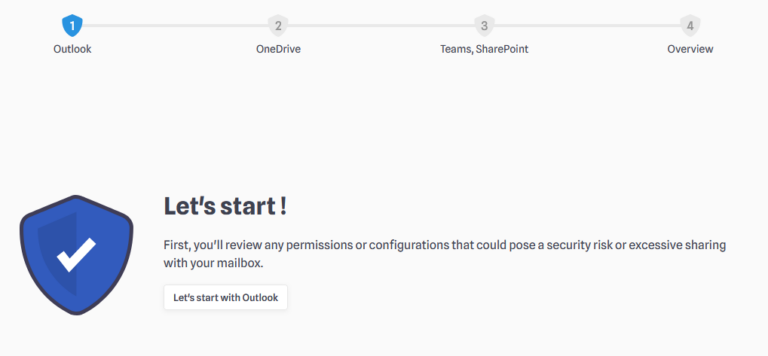
You will then be guided through different pages, depending on the nature of your POAs. Here are some information you will find in each page :
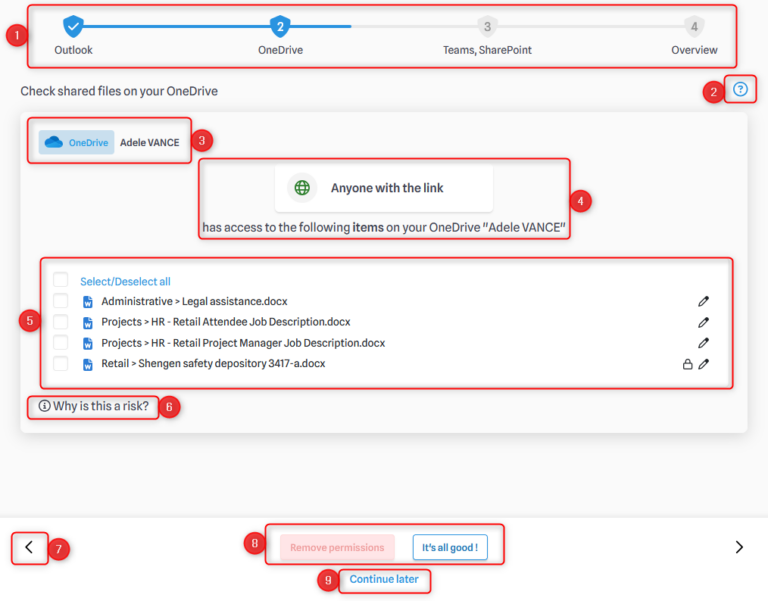
- On every page, you can track your progress through the Security Checkup.
- If you need assistance, click here to activate the tutorial.
- Indicates which resource is currently being reviewed.
- Displays the type of POA you are reviewing.
- Lists all files or folders at risk; when you select one or more, you can choose to remove the permissions granted on them.
- Click here if you want more information about the risk associated with this POA.
- Click here to return to the previous screen.
- This is where you can choose to remove permissions (after selecting one or more files/folders), or click “Everything’s fine” if you wish to keep all permissions.
- If you click here, you will be redirected to your MyDataSecurity profile. The Security Checkup will remain available on the home page until it is completed.
When you reach the end of the Security Checkup, you will get to this screen :
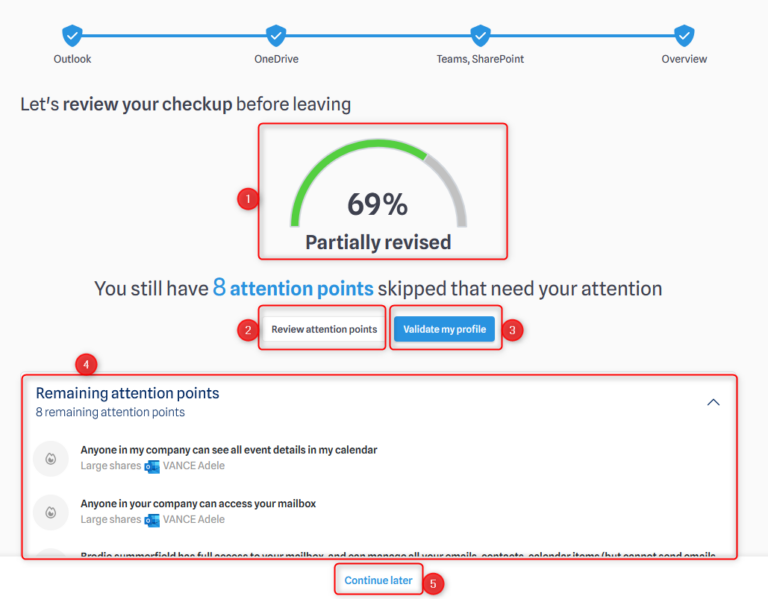
- Indicates how far you have progressed in reviewing your POAs.
- Click here if you want to review the remaining POAs.
- If you believe everything is in order, you can validate your profile here. This means the remaining POAs will no longer be marked in red, as validation indicates that you consider them valid.
- The list of remaining POAs.
- If you can’t complete your review or want to come back later, this will redirect you to your profile homepage.
Points of attention (POAs) highlight the most significant security threats in your profile, for example:
☑ Sharing of sensitive files based on the labels provided by your classification system (AIP/MIP)
☑ External, anonymous, extended file sharing
☑ External e-mail transfers
☑ Etc.
when you open your profile, you might see a white rectangle with the list of your POAs. If you don’t see this menu, please go directly to the previous tab “Security Checkup”
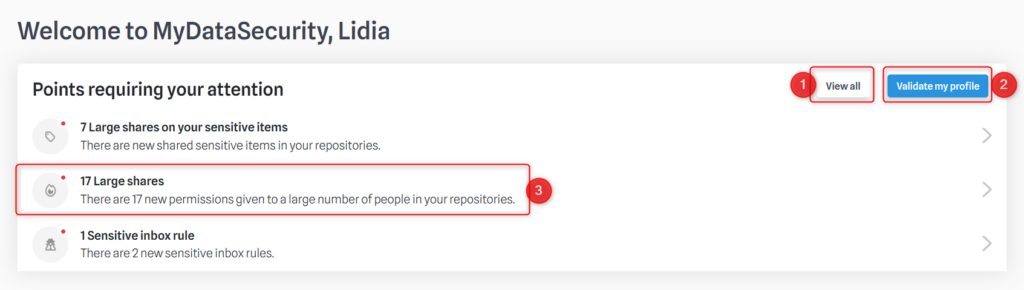
- Gives access to a modal containing the extensive list of all POAs on your profile
- Clicking on this button confirms that you consider the POAs to be verified. Caution! Once attention points have been hidden, they no longer appear in this list, and the red dots disappear.
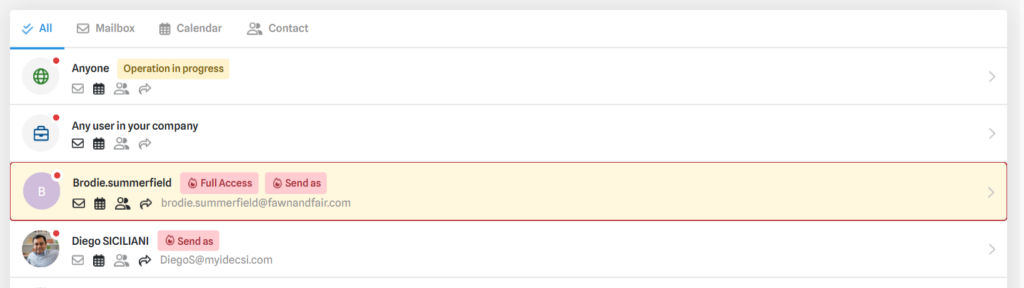
- By clicking on one of your points of attention, you will be redirected to the corresponding tab (OneDrive, Outlook etc.). The focus will then be highlighted, as in the example below:
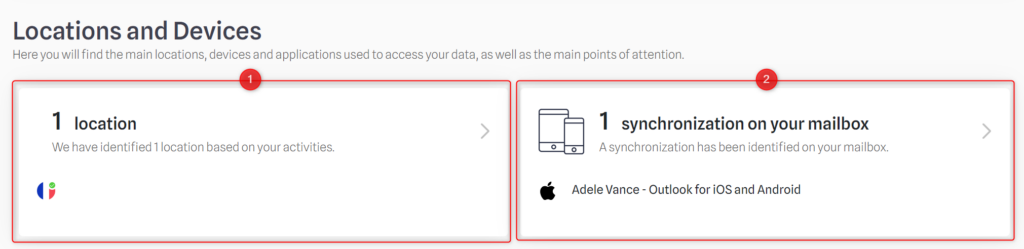
- Click on Locations to access the list of connection countries and their validity period (if access from this country is temporary)
Click on synchronizations to access the list of devices or applications (computer, mobile, tablet, etc.) where your mailbox has been synchronized.
Locations modal and remediation
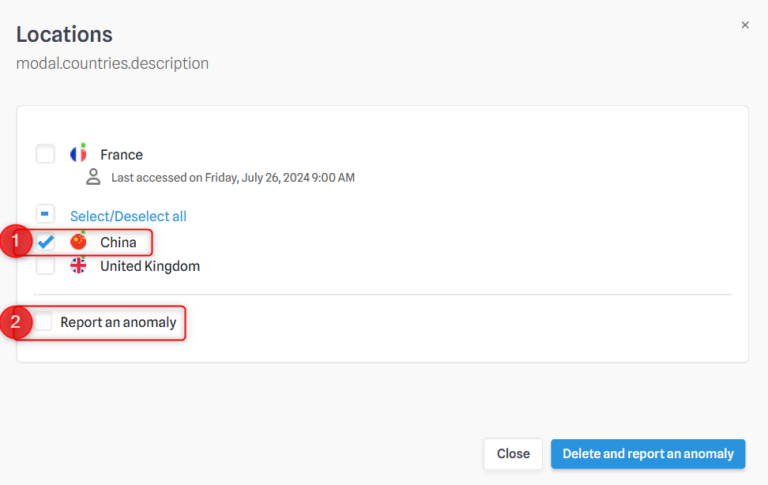
- You can select a country and click on “delete” if you no longer plan to log in from that country.
It is also possible to check the “Report an anomaly to security team” box if a connection seems suspicious.
Devices modal and remediation
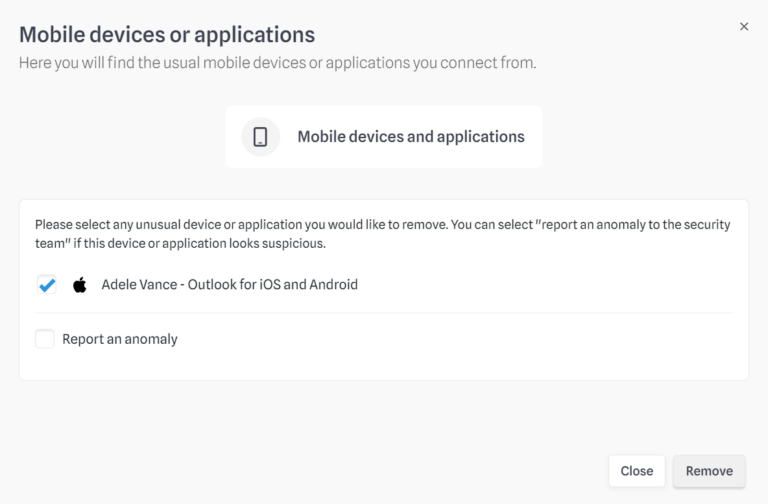
As for countries :
You can select a device and click on “delete” if you no longer plan to connect from it.
You can also check the box “Report an anomaly to the security team” if a connection seems suspicious (*).
*This deletion and reporting option is available for all points of attention / permissions / security risks displayed on MyDataSecurity, and will no longer be specified in this document
- Additional menu to access all your Microsoft 365 resources.
💡 The presence of a red dot indicates the existence of POAs to be checked throughout the security profile. (Optional) Additional resources to help you get the most out of MyDataSecurity
*These options are only available for IDECSI Advanced® (and not for IDECSI Detox®)